We occasionally get asked about the specifics of Bluetooth LE security. This is usually when a project has security requirements or needs to formally document things such as cryptography schemes and vulnerabilities.
The U.S. Department of Commerce National Institute of Standards and Technology (NIST) has an informative Guide to Bluetooth Security (pdf) that provides information on the security features of Bluetooth, vulnerabilities, threats and extensive recommendations.
The following table provides an overview of Bluetooth LE compared ‘Classic’ Bluetooth Basic Rate/Enhanced Data Rate (BR/EDR) protocol:
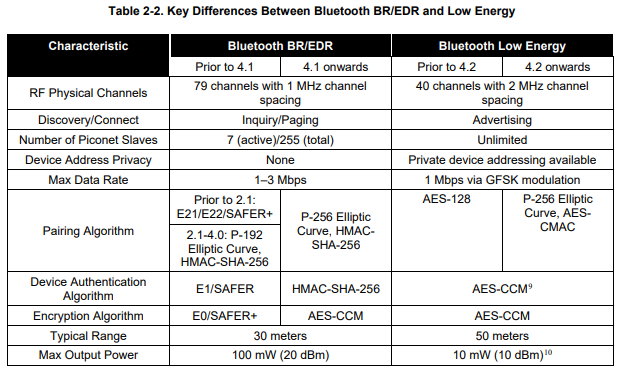
Bluetooth LE 4.2 and later uses ECDH P-256 Elliptic Curve public key cryptography for protection against passive eavesdropping and man in the middle (MITM) during pairing.
While it’s good for projects to be aware of the underlying mechanisms and their limitations, we find that, in practice, security threats and weaknesses tend to be related more to how Bluetooth LE is used (by software) on a particular project rather than Bluetooth implementation itself.