It’s interesting how many of our clients come to us with a problem to solve and in talking through possible solutions they often suddenly have the thought, ‘That’s IoT isn’t it?’. They weren’t looking for an IoT or Industry 4.0 solution but they got there by a different route. Indeed, it’s always best to start by solving problems rather than trying to fit technology into existing processes.

So what are the typical problems in factories? While companies usually have systems to take orders and invoice for them, what goes on in between is often a manual paper process. Knowing where an order is physically and hence how far it has been completed often requires lots of ringing round. Similarly, there are usually problems finding parts for jobs. Parts arrive in boxes or in pallets and are stored somewhere pending jobs. Finding the right pallet or box on a large site can be a challenge. It might be in storage, already on the factory floor somewhere or in transit between areas. Sometimes, delicate parts might be left in the wrong places and spoil due to excess humidity or in some cases incorrect temperature. Expensive tools and equipment tends to be shared between work areas and this can also get mislaid, lost or stolen.
All these problems cause delays in production, reduced productivity, incur penalties or future lost orders due to delayed work and cause employee frustration.
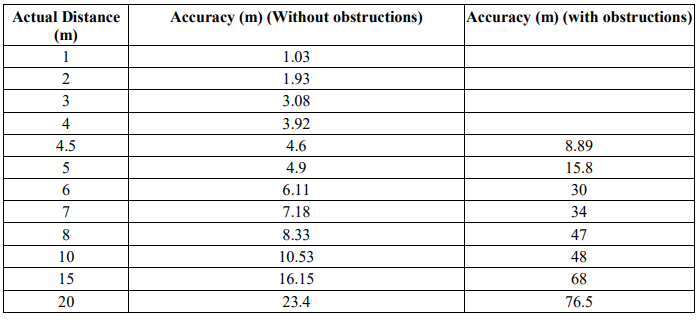
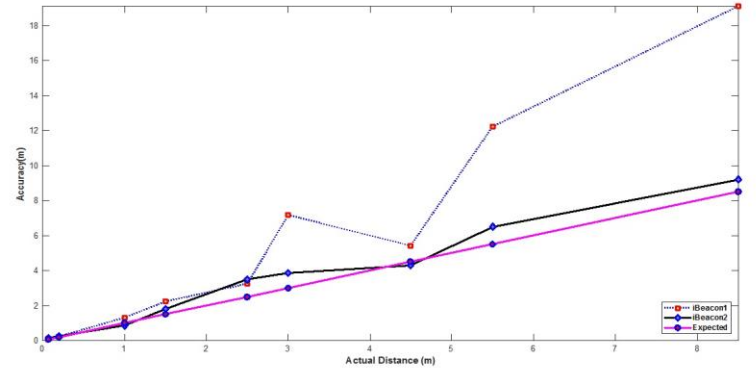
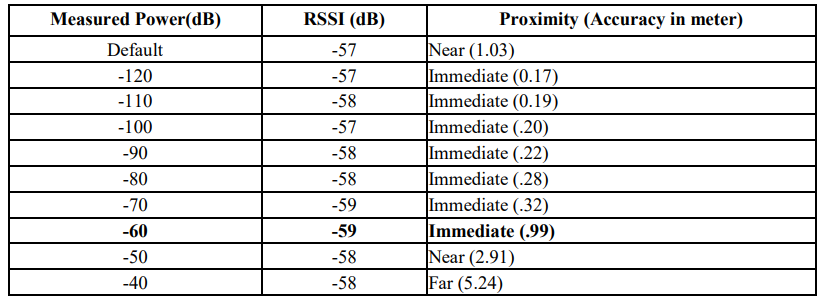
The solution is to better track jobs, parts, sub-assemblies and shared valuable tools so that they can be located on factory plans. This tracking needs to be continuous and real-time because merely scanning things in/out using barcodes is open to human error and location is otherwise only as good as the last scan. Historical data shows where things have been in the past. Analysis of this data allows blockages to be identified so that the process as a whole can be refined to improve efficiency and production.
The result is reduced downtime, less time re-ordering or re-making things that have been lost, optimum productivity and better use of skilled staff doing their job rather than searching for things.
Read about Beacons in Industry and the 4th Industrial Revolution (4IR)