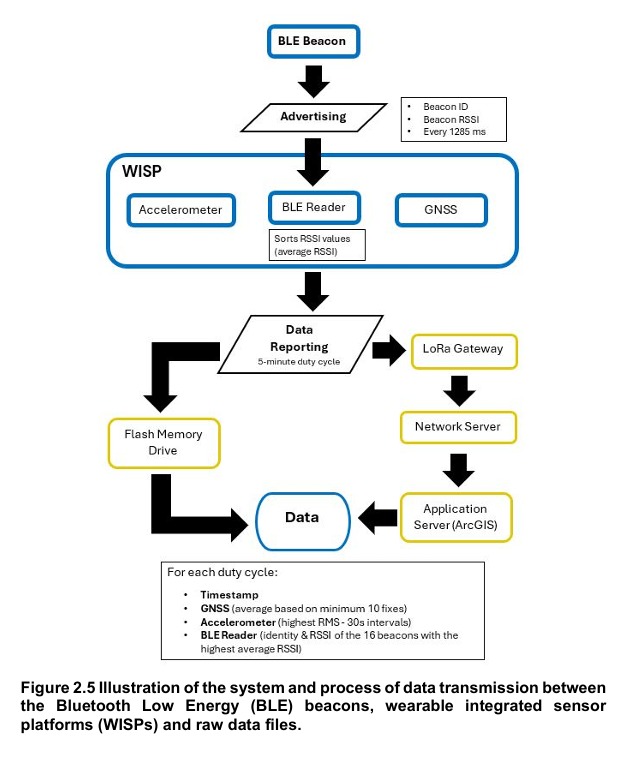
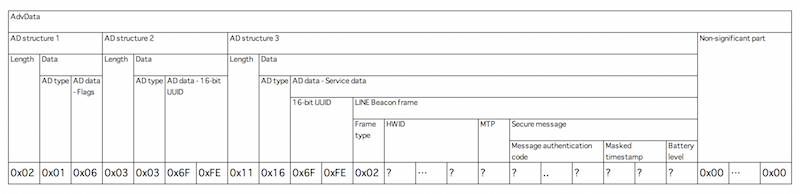
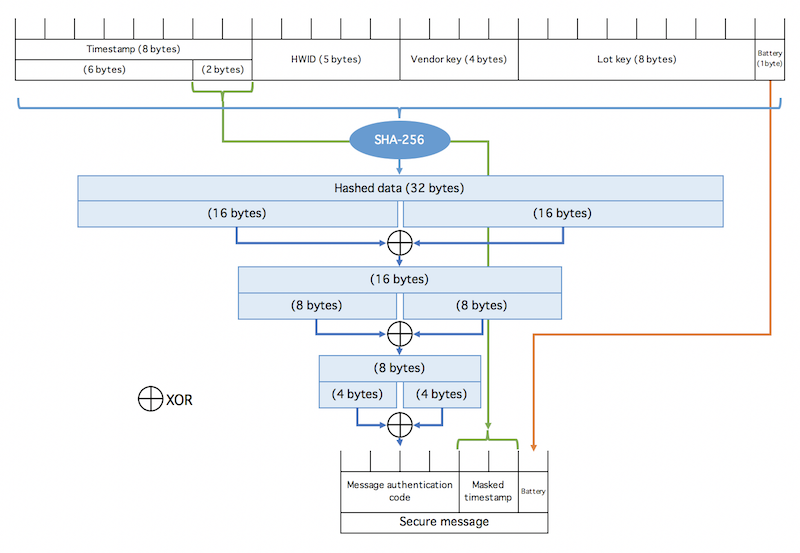
Beacons don’t generally need to store data because they are just sending out their unique id. However, sensor beacons do sense values over time that you might want to collect later via, for example, an app coming close to the beacon. Specialist devices such as social distancing beacons need to store close contacts for later collection.
It is a misconception that beacons send data directly to smartphones when they come into proximity. In reality, beacons only transmit a small identifier, not the actual content or data itself. This identifier is then matched to information stored elsewhere, either on the user’s device or on a remote server. The relevant app, or app calling a server, uses this match to retrieve and display the appropriate data to the user.
Beacons use a System on a Chip (SoC), such as the Nordic nRF51, that includes memory. Most of the memory is used for the internal functioning of the beacon. Newer versions of SoC, for example the Nordic nRF52, have more memory that allows data to be stored.

There are some sensor logger beacons that store sensor values but this tends to be restricted to temperature logging.