A recent study with the strange title SoK: The Long Journey of Exploiting and Defending the Legacy of King Harald Bluetooth (pdf) provides a comprehensive analysis of the security and privacy issues surrounding Bluetooth technology. Authored by Jianliang Wu, Ruoyu Wu, Dongyan Xu, Dave (Jing) Tian, and Antonio Bianchi from Purdue University and Simon Fraser University, it explores the evolution of Bluetooth security over 24 years, focusing on both attacks and defences.
The paper begins by summarising the evolution of Bluetooth security features since its first version, discussing the introduction of Bluetooth Low Energy (BLE) and Mesh protocols. It then looks into a systematisation of 76 attacks and 33 defences, categorising them based on their affected layers in the Bluetooth stack, the protocols they target, and their threat models.
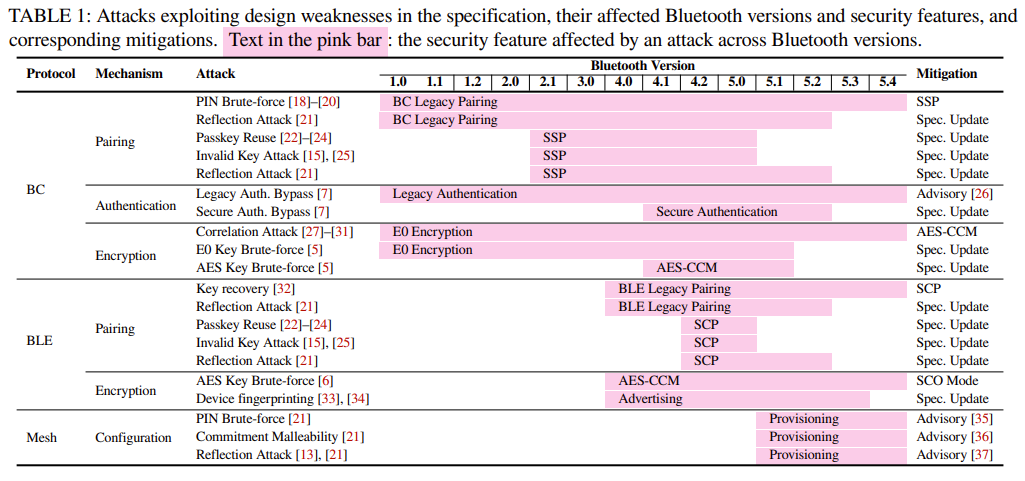
Key observations include the increasing number of privacy attacks during the BLE device discovery phase, challenges in pairing security due to user mistakes and a mismatch between the assumptions of Bluetooth specifications and their real-world implementations on modern operating systems. The authors also highlight that while Bluetooth’s security has improved over time, there remain significant gaps in both security and privacy features that need addressing.
The document further explores attacks and defences in detail, divided into different layers of the Bluetooth stack: the physical layer, firmware layer, and host layer. Each layer faces unique challenges, from signal eavesdropping and injection at the physical layer to firmware exploitation and host exploitation attacks. The authors categorise these attacks based on their goals, affected protocol, phase, and attack model, providing a comprehensive overview of the current state of Bluetooth security.